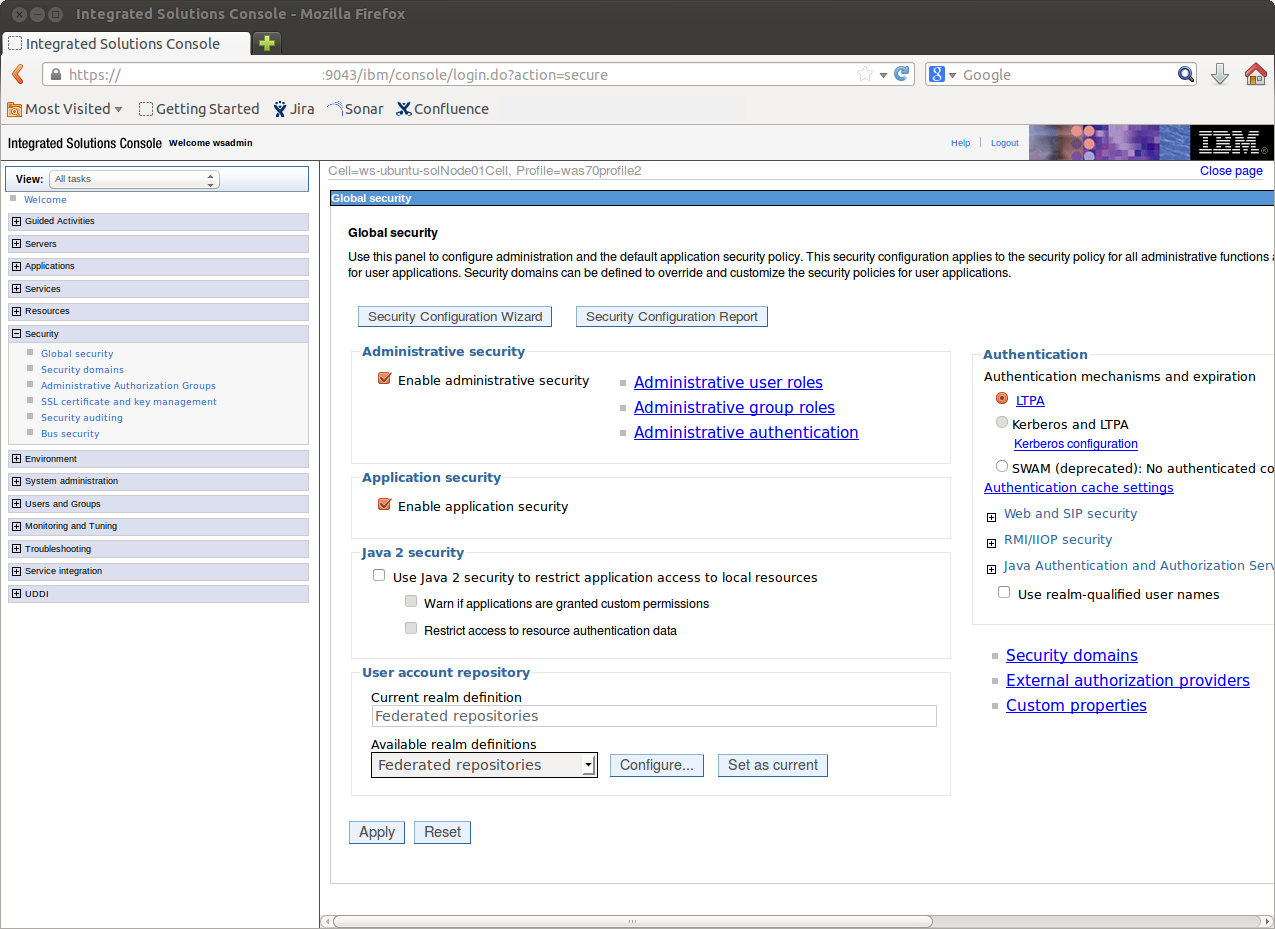
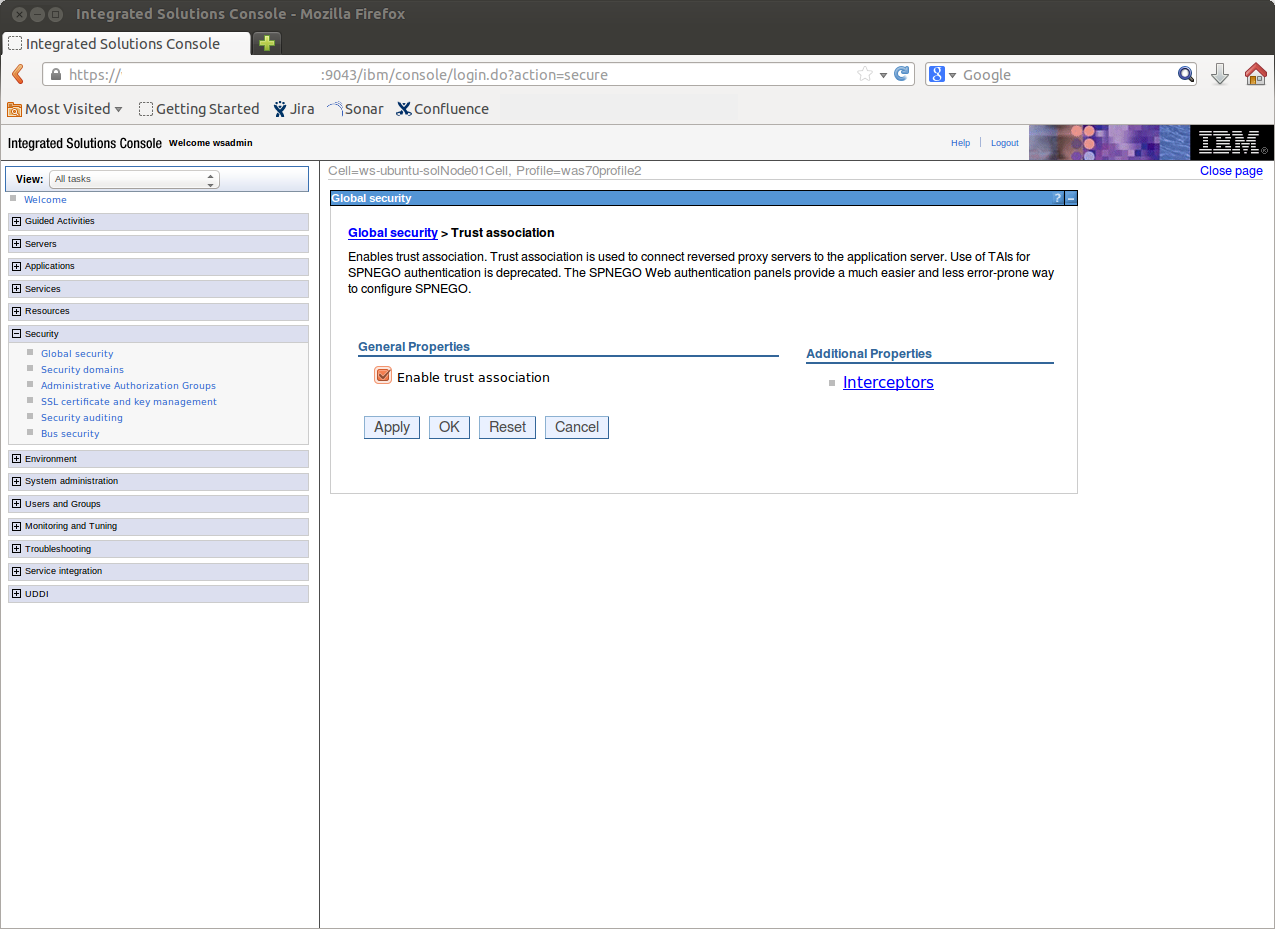
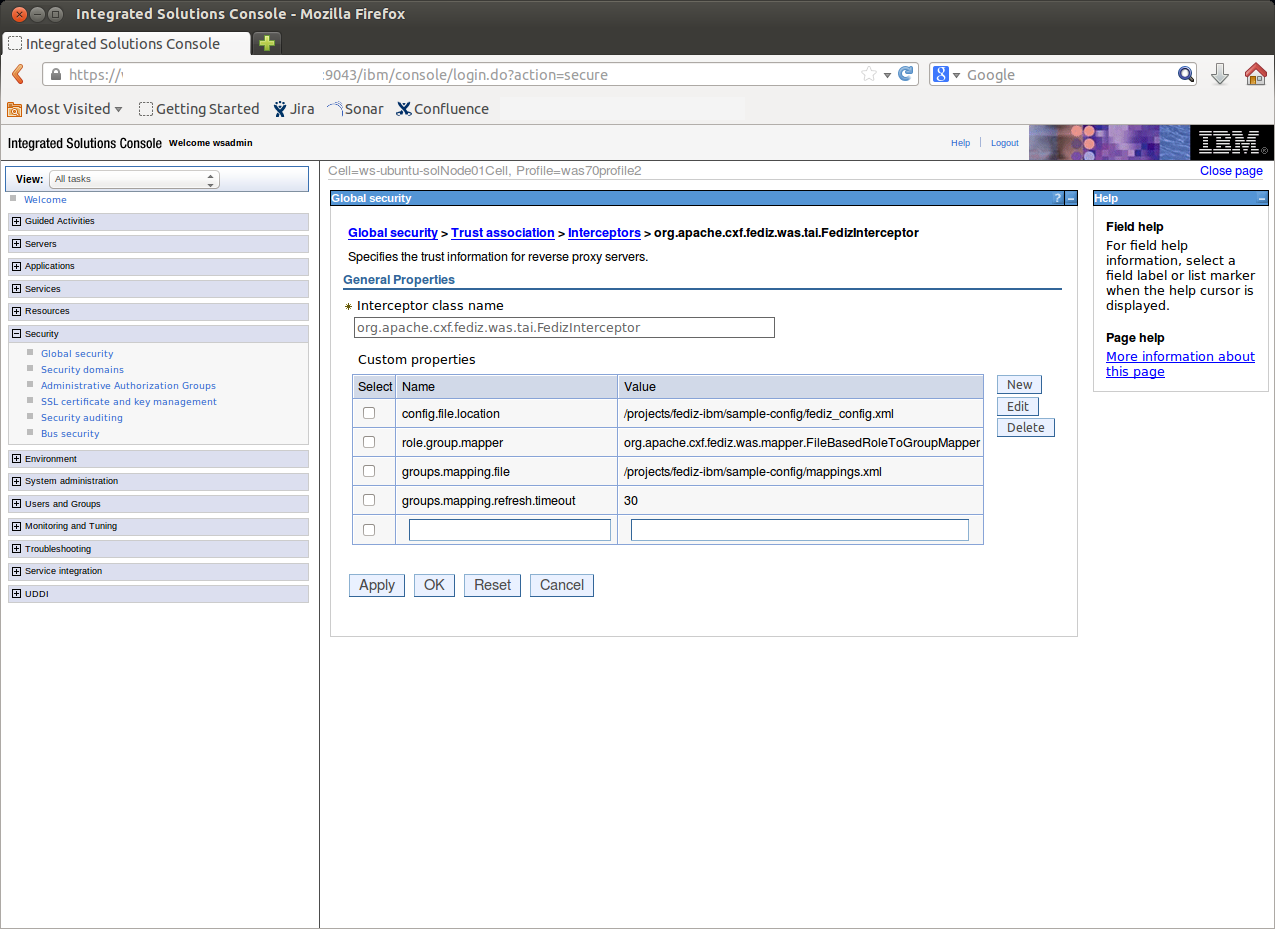
IBM Websphere PluginApache CXF Fediz ships a plugin to secure an IBM Websphere 7/8 Application Server using WS-Federation. This page describes how to enable Federation for a IBM Websphere Application Server (WAS) instance hosting Relying Party (RP) applications. This configuration is not for a Websphere instance hosting the Fediz IDP and IDP STS WARs but for applications that use SAML assertions for authentication. After this configuration is done, the Websphere-RP instance will validate the incoming SignInResponse created by the IDP server. Prior to doing this configuration, make sure you've first deployed the Fediz IDP and STS on the separate Servlet Container instance as discussed here, and can view the STS WSDL at the URL given on that page. That page also provides some tips for running multiple Tomcat instances on your machine. Websphere SecurityA Trust Authentication Interceptor (TAI) is a pluggable security component that is installed and configured at the IBM WebSphere Application Cell level. As such, any managed server on the Cell will have this component installed in and activated once defined in the WAS Security configuration. The Fediz Plugin for Websphere provides a TAI implementation which leverages the Fediz Core. WAS security runtime supports a notion of a security session using a specific security token called LTPA Token which is implemented as a HTTP cookie. The cookie lifetime is specified at the WAS administrative Cell level, which implies that it is not possible to configure this value per request based on the requirements for an application. Build Fediz Websphere LibraryYou have to build the Fediz plugin on your own as it depends on IBM Websphere libraries.
InstallationPre-RequisitesThe Administrative and Application security must be activated for the WAS security layer to be able to intercept secured resources access requests. The local User Registry must be properly configured and at least one group of users must be declared in the registry prior any application installation. Plugin InstallationThe Fediz Websphere plugin and its dependencies must be copied in the The Fediz configuration file (ex. Web Application configuration
The file defined in roleGroupMapping.xml
<?xml version="1.0" encoding="UTF-8"?>
<mapping>
<samlToJ2EE>
<claim>User</claim>
<groups>
<j2eeGroup>Authenticated</j2eeGroup>
<j2eeGroup>Users</j2eeGroup>
</groups>
</samlToJ2EE>
<samlToJ2EE>
<claim>Manager</claim>
<groups>
<j2eeGroup>Manager</j2eeGroup>
<j2eeGroup>Authenticated</j2eeGroup>
</groups>
</samlToJ2EE>
<samlToJ2EE>
<claim>Admin</claim>
<groups>
<j2eeGroup>Admin</j2eeGroup>
<j2eeGroup>Authenticated</j2eeGroup>
</groups>
</samlToJ2EE>
</mapping>
A role value defined in element Fediz configurationThe Fediz related configuration is done in a Servlet Container independent configuration file which is described here. Federation Metadata documentThe Webpshere Fediz plugin supports publishing the WS-Federation Metadata document which is described here. |