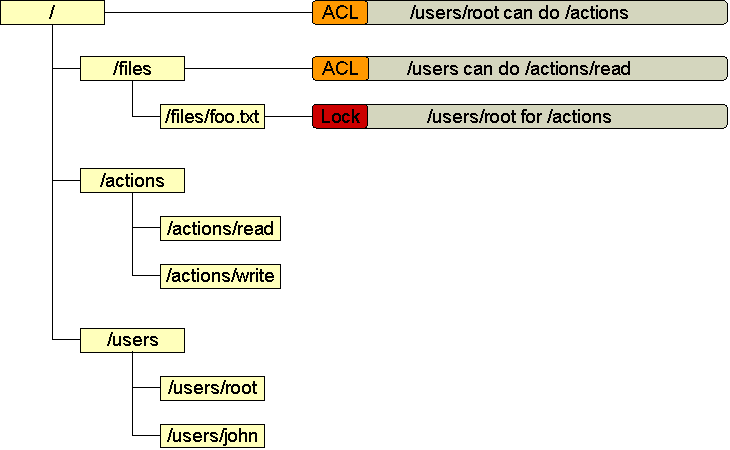
Every ObjectNode has associated permissions, which are tuples with the following format:
(target subject, executing subject, action, inheritance)
Here are examples of permissions:
(/foo/document.txt, /user/dave, /actions/read, no)
(/foo/document.txt, /user/dave, /actions/write, no)
(/foo, /user/john, /actions/read, yes)
Permissions granted on an object are inherited (unless specified otherwise during permission assignement) by the children of the object. For example, a permission specified on object whose URI is /foo would be inherited by object /foo/bar.
This inheritance behavior also applies to subjects and actions. Subject /users/dave will have all the permissions given to all the subject /users. Likewise, a subject who can perform action /actions on an object will be able to perform /actions/read.



