Agent to Application Master SSL Communication¶
Slider agents are configured to communicate with the Slider Application Master using SSL. By default, one-way SSL authentication is enabled (i.e., the agent verifies the identity of the application master). However, two-way SSL authentication can be enabled to further secure the communication channel.
Application Master SSL Support¶
There are two primary components enabling server-side SSL support:
- The server's certificate mananger
- The agent-facing HTTPS Server
Server Certificate Manager¶
As the Slider application master starts up it leverages the certificate manager to ensure that the resources required to support SSL transport - the server certificate, the key store, and the truststore - are available. The certificate manager will create these artifacts if necessary (see figure 1).
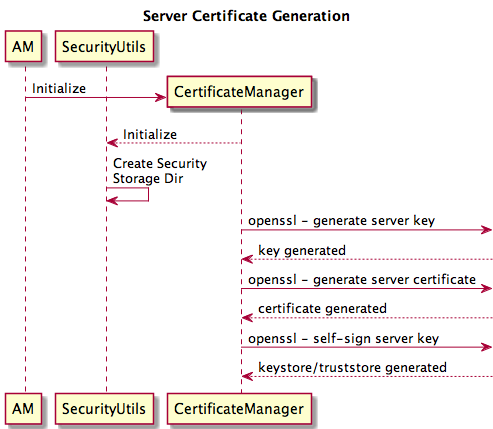
Figure 1 - Server Certificate and Keystore/Trustore Generation
In addition, if two-way SSL is enabled (more on that later), the Slider application master will leverage the certificate manager to create client certificates for every container launched as part of the application. These certificates, along with the AM's certificate, will subsequently be seeded to the given container's host machine via Yarn's resource localization facilities.
Agent-facing HTTPS Server¶
Once the artifacts necessary for supporting SSL transport are available, the agent-facing HTTP server instance is created and started. This instance creates two SSL connectors. The first connector is always configured for one-way SSL and supports server liveness checks from the agents. The second connector provides the port over which agent registration and heart beats are transmitted. It is configured for one-way SSL by default but can be explicitly configured for two-way SSL (hence the need for a certificate seeding mechanism as detailed above). Figure 2 illustrates this startup sequence.
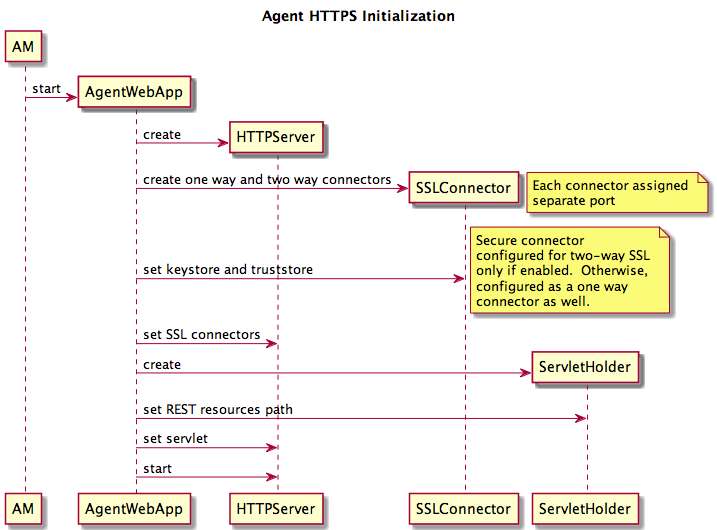
Figure 2 - Server Agent-facing HTTP Server Initialization
Agent Communication Modes¶
The agent and application master communicate over HTTPS in one of two modes:
- One-way SSL
- Two-way SSL
One-way SSL¶
This is the default communication mode between the agent and application master. One-way SSL authentication requires the client to verify the identity of the server, but the server does not verify the identify of the client (in this case, the agent).
The sequence of events for the setup of agent to AM one-way SSL communication is:
- The Agent attempt to connect to the AM's one-way SSL port (see Agent HTTPS server discussion above).
- If the agent receives an HTTP OK response (Status 200), it proceeds with sending a registration request to the AM over the secured port (in this case, also configured for one-way SSL).
- Once the agent receives the registration response, it proceeds with the sending of heartbeat messages.
See Figure 3 for an illustration of this sequence.
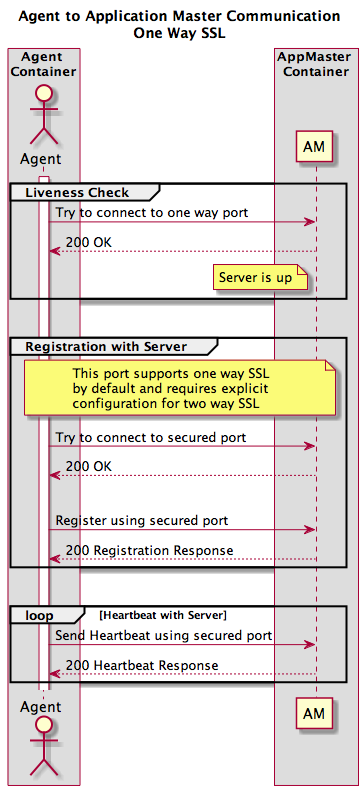
Figure 3 - Agent to AM One-way SSL Communication
Two-way SSL¶
The setup for two-way SSL is more involved since both parties must have each other's certificates available to establish the trust required for this authentication mechanism. Therefore, the Application Master seeds both the AM's certificate (trust store) and the client's certificate (key store) to the host machine as the container is being instantiated. Therefore, the two parties are configured for communication over the configured two-way SSL port. See Figure 4 for an illustration of this setup.
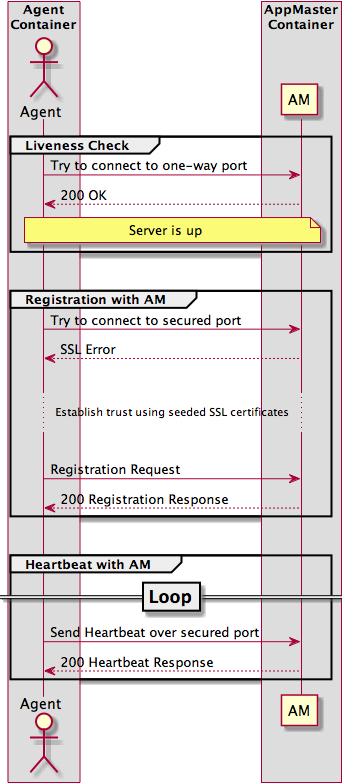
Figure 3 - Agent to AM Two-way SSL Communication
Note that two-way SSL is enabled by setting a property ("ssl.server.client.auth") for the slider application master in the application configuration:
"components": { "slider-appmaster": { "jvm.heapsize": "256M", "ssl.server.client.auth": "true" } }

